How to Configure UFW to block ICMP Request On Ubuntu 22.04 Server
Image by Arief JR
UFW is stand for Uncomplicated Firewall, the program is for managing a netfilter firewall designed to be easy to use. Blocking ICMP (Internet Control Message Protocol) requests can help prevent certain types of network attacks, such as ping floods. Here is how you can block ICMP requests on Ubuntu 22.04:
- Using ufw (Uncomplicated Firewall):
ufw is a frontend for iptables, designed to simplify the process of configuring a firewall. Here’s how you can block ICMP requests using ufw:
Open a terminal.
Block incoming ICMP requests by adding a rule to ufw:
1
sudo ufw deny proto icmp from any to any
- Reload ufw to apply the changes:
1
sudo ufw reload
- Using iptables:
iptables is a more advanced tool for configuring the Linux kernel’s netfilter firewall. Here’s how you can block ICMP requests using iptables:
- Open a terminal.
- Add a rule to drop ICMP echo-request packets:
1
sudo iptables -A INPUT -p icmp --icmp-type echo-request -j DROP
- To make this change persistent across reboots, you need to save the iptables rules:
1
2
sudo apt install iptables-persistent
sudo netfilter-persistent save
- Using sysctl to disable ICMP responses:
This method involves changing kernel parameters to disable ICMP responses.
- Open a terminal.
- Edit the /etc/sysctl.conf file:
1
sudo nano /etc/sysctl.conf
- Add the following line to the file:
1
net.ipv4.icmp_echo_ignore_all = 1
- Apply the changes:
1
sudo sysctl -p
- Block using ufw rules, ensure ufw is enabled:
- Open terminal:
1
sudo ufw enable
- Block ICMP echo requests (ping requests): You can add a rule to block incoming ICMP echo requests by editing the before.rules file in the ufw configuration. Open the before.rules file with your preferred text editor (e.g., nano):
1
sudo nano /etc/ufw/before.rules
- Add the following lines to block ICMP echo requests: Add these lines at the beginning of the file, just after the comments section:
1
2
# Block ICMP echo requests
-A ufw-before-input -p icmp --icmp-type echo-request -j DROP
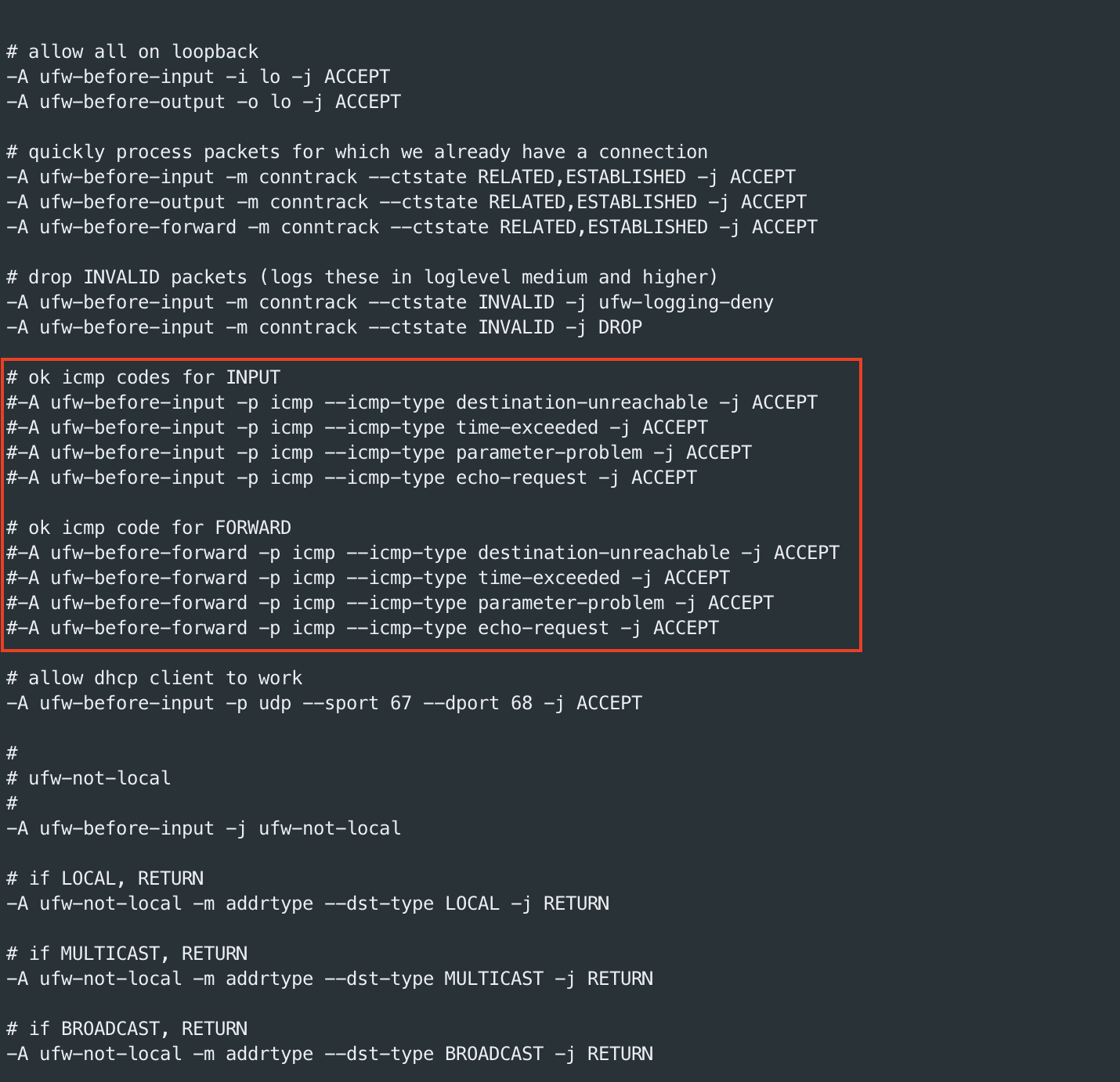
- Or you can comment this line without add the above line:
From this:
1
2
3
4
5
6
7
8
9
10
11
# ok icmp codes for INPUT
-A ufw-before-input -p icmp --icmp-type destination-unreachable -j ACCEPT
-A ufw-before-input -p icmp --icmp-type time-exceeded -j ACCEPT
-A ufw-before-input -p icmp --icmp-type parameter-problem -j ACCEPT
-A ufw-before-input -p icmp --icmp-type echo-request -j ACCEPT
# ok icmp code for FORWARD
-A ufw-before-forward -p icmp --icmp-type destination-unreachable -j ACCEPT
-A ufw-before-forward -p icmp --icmp-type time-exceeded -j ACCEPT
-A ufw-before-forward -p icmp --icmp-type parameter-problem -j ACCEPT
-A ufw-before-forward -p icmp --icmp-type echo-request -j ACCEPT
To this:
Save and close the file: If you are using nano, you can save and exit by pressing CTRL+X, then Y to confirm changes, and Enter to save the file.
Reload ufw to apply the changes:
1
sudo ufw reload
- Verify the rules: You can check the status and the rules applied by using:
1
sudo ufw status verbose
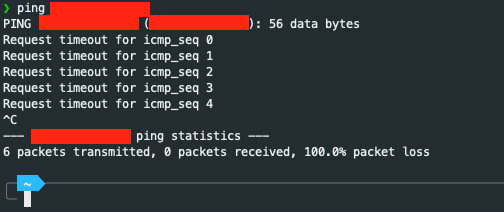
- Test ping
test ping to destination ip address after changed in above:
1
ping <your ip address>
The result will be like this:
This should show you the current rules, including the one you added for blocking ICMP echo requests.
Choose the method that best fits your needs. Each of these methods provides a way to block ICMP requests, enhancing the security of your Ubuntu system. These steps will effectively block incoming ICMP echo requests on your Ubuntu 22.04 server, thereby preventing it from responding to ping requests.